



![]() Point(s) of Contact
Point(s) of Contact
Pamela Hamilton / FSO

843.327.3273
pamela@appliedsecurityknowledge.com
Richard Carmichael / ITPSO
678.221.7834
rcarmichael@laochservices.com

DoD Hotline
dodig.mil/hotline / 800.424.9098
SOURCE: DCSA
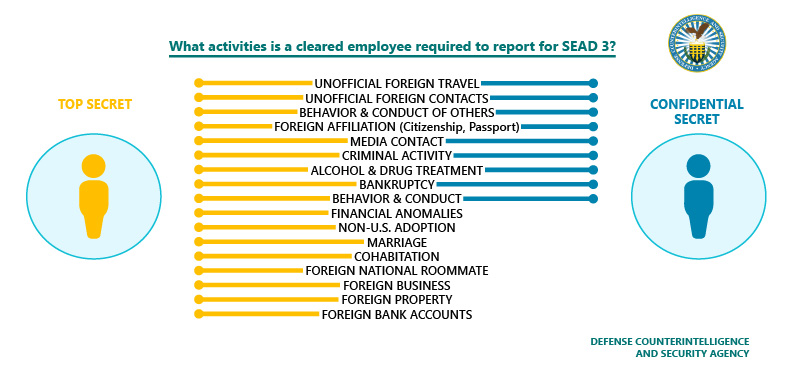
This could be your defining moment. The SEAD 3 was established and released as reporting requirements across the federal government for all "Covered individual" who have access to classified information or hold a sensitive position. Read the list below of "Covered Individuals" to see if your position with a defense contract company is considered a "Covered Individual":
The following link includes various scenarios that will help you determine if a situation or activity you are participating in is considered "reportable":
Go to SEAD 3 Reporting Details / Scenarios
SOURCE: Navy Times by Geoff Ziezulewicz – January 26, 2022
Roughly a month before the start of the largest federal trial in the so-called "Fat Leonard" scandal, another Navy officer pleaded guilty Wednesday to taking bribes from foreign defense contractor Leonard Glenn Francis in exchange for classified ship schedules and other information, the U.S. Justice Department announced Wednesday.
Cmdr. Stephen Shedd, 48, pleaded guilty in a San Diego court to bribery charges and admitted that he and eight other Navy members "received more than $250,000 in meals, entertainment, travel and hotel expenses, gifts, cash and the services of prostitutes" from Francis, the rotund port services magnate, His company, Glenn Defense Marine Asia, provided husbanding services to ships in the U.S. 7th Fleet for years, according to the Justice Department.
Shedd and eight others were indicted in March 2017 for conspiring with and receiving bribes from Francis.
He becomes the third of those original nine defendants to plead guilty ahead of the trial, which has been delayed several times and is now scheduled to begin on Feb. 28.
SOURCE: Gov Info Security by Dan Gunderman – February 14, 2022

CISA Director Jen Easterly (Photo: New America via Flickr/CC)
The U.S. Cybersecurity and Infrastructure Security Agency has issued a "Shields Up" alert to U.S. organizations to protect against potential retaliatory cyberattacks at the hands of the Russians - especially if the Biden administration intervenes in the country's conflict with Ukraine, where Russia has massed some 100,000 troops.
In the latest alert, CISA says, "The Russian government has used cyber as a key component of their force projection over the last decade, including previously in Ukraine in the 2015 timeframe. The Russian government understands that disabling or destroying critical infrastructure - including power and communications - can augment pressure on a country's government, military and population and accelerate their acceding to Russian objectives."
CISA says it is not aware of "any specific credible threats to the U.S. homeland," but that it is "mindful of the potential for the Russian government to consider escalating its destabilizing actions in ways that may impact others outside of Ukraine."
In response, the nation's operational cyber agency says it is working with critical infrastructure partners to "ensure awareness of potential threats."
SOURCE: Nextgov by Alexandra Kelley – January 25, 2022

The National Institute of Standards and Technology issued its newest and final copy of guidance for organizations to assess their internal security IT systems, following a draft copy and comment period.
The document, titled "Assessing Security and Privacy Controls in Information Systems and Organizations," focuses on helping entities manage cybersecurity risks across their individual networks.
"The updated publication provides an assessment approach and procedures—i.e., how to determine if the countermeasures are implemented and achieving the desired effect," NIST said in an email to Nextgov.
Guidelines included in the final draft emphasize improving organizational assessments of current cybersecurity infrastructure, promoting better cybersecurity awareness among users, enabling cost-effective security assessment procedures and privacy controls, and creating reliable security information for executives.
NIST officials thoroughly review best practices in assessment procedures to determine the effectiveness of the defense software in place. Three phases are associated with this testing, broadly including: preparing, conducting and analyzing assessment results to gauge risk.

Since November 2021, ransomware groups have targeted U.S. cleared defense contractors via ground shipping mail. Bad actors are sending USB flash drives containing malicious code to lure companies to use them and infiltrate their information systems. Once recipients plug in the flash drive, the device executes a cyberattack, in which the flash drive registers itself as a keyboard and sends a series of preconfigured automated keystrokes to the user's device to gain administrative rights to install ransomware. NEVER use a USB flash drive when you don't know its pedigree! ALWAYS assume the worst and stay secure!
Reporting mental health: security professionals understand that when individuals candidly report their conditions and seek mental health care in accordance with their practitioner's recommendations, psychological conditions are not security concerns in the vast majority of cases. That said, curiosity about how adjudicators resolve affirmative answers to Section 21 is understandable and the following offers some insight:
If security concerns remain after these inquiries, the security professional may ask for the applicant to participate in an evaluation with a psychologist or psychiatrist who will consider possible security risks associated with the condition. Keep in mind that these security evaluations are quite rare. For NISP contractors, usually fewer than 300 evaluations a year are requested, and a majority of those determine the applicant's psychological condition does not present security concerns.