



![]() Point(s) of Contact
Point(s) of Contact
Pamela Hamilton / FSO

843.327.3273
pamela@appliedsecurityknowledge.com
Richard Carmichael / ITPSO
678.221.7834
rcarmichael@laochservices.com

DoD Hotline
dodig.mil/hotline / 800.424.9098
SOURCE: ABC News 4 by Angie Moreschi, Nathan Aaron, Larry Deal & Liz Gonzalez – July 18, 2024
Having your account spoofed or hijacked on social media platforms like Facebook and Instagram can quickly turn into a nightmare.
Spotlight on America discovered there's been a sharp increase in complaints nationwide regarding social media-related identity theft. What's worse is that all too often social media companies do little to help their own users who've been hacked.
SOURCE: FOX NEWS by Landon Mion – August 14, 2024

An electrical engineer working with the Air Force is accused of printing over 150 pages of "top secret" government documents before attempting to flee the country for Mexico, according to prosecutors.
Gokhan Gun, 50, was arrested Friday as he was departing for a flight to Puerto Vallarta, Mexico. Gun, a northern Virginia resident who was born in Turkey and holds dual citizenship, was charged with unauthorized removal and retention of classified material, according to Fox 5 DC.
On Friday morning, Gun was leaving for the airport when FBI agents executed a search warrant on him and two of his homes. Agents discovered documents marked as "TOP SECRET" inside a backpack in front of his home. They also found stacks of documents in the dining room of his home with visible classification markings, including some marked as Top Secret and SCI, or Sensitive Compartmented Information.
SOURCE: UtilityDrive by Matt Kapko – August 12, 2024

LAS VEGAS — For Cybersecurity and Infrastructure Security Agency Director Jen Easterly the doomed CrowdStrike software update that took global IT systems and networks offline last month holds a "big lesson" for critical infrastructure.
"The CrowdStrike incident was such a terrible incident," Easterly said Wednesday during a media briefing at the Black Hat cybersecurity conference, but "it was a useful exercise, like a dress rehearsal for what China may want to do to us."
The outage was not the result of a malicious act, but rather a basic field input error that caused an out-of-bounds memory read. Yet, to Easterly, the widespread chaos it caused offers a clear example of what could occur if China-affiliated attackers make good on its efforts to cause systemic disruption to U.S. critical infrastructure.
When Easterly learned of the outage, around 2 a.m. on July 19: "What was going through my mind was 'oh, this is exactly what China wants to do.'"
SOURCE: WIRED by Matt Burgess – August 8, 2024
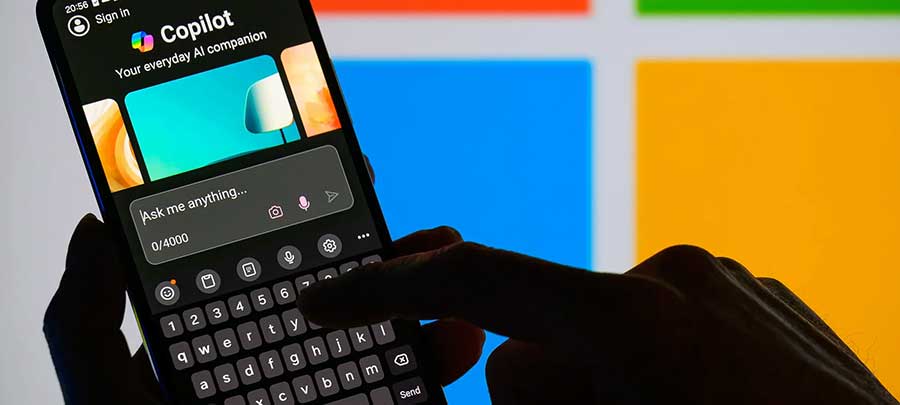
Microsoft raced to put generative AI at the heart of its systems. Ask a question about an upcoming meeting and the company's Copilot AI system can pull answers from your emails, Teams chats, and files—a potential productivity boon. But these exact processes can also be abused by hackers.
Today at the Black Hat security conference in Las Vegas, researcher Michael Bargury is demonstrating five proof-of-concept ways that Copilot, which runs on its Microsoft 365 apps, such as Word, can be manipulated by malicious attackers, including using it to provide false references to files, exfiltrate some private data, and dodge Microsoft's security protections.
One of the most alarming displays, arguably, is Bargury's ability to turn the AI into an automatic spear-phishing machine. Dubbed LOLCopilot, the red-teaming code Bargury created can—crucially, once a hacker has access to someone's work email—use Copilot to see who you email regularly, draft a message mimicking your writing style (including emoji use), and send a personalized blast that can include a malicious link or attached malware.
SOURCE: ClearanceJobs by Lindy Kyzer – July 29, 2024
Having the right clearance eligibility for a specific position is a critical part of the national security hiring process. A Secret clearance is not the same as a Top Secret/SCI. For contractors, specifically, with task orders that require them to fill positions with individuals possessing a very specific set of skills and abilities, clearance level matters.
That's why some recruiters get confused with a well-intentioned Facility Security Officer (FSO) or Defense Counterintelligence and Security Agency (DCSA) rep flags their job listings and says they need to remove the clearance designations because the listings violate a rule for companies about 'advertising' their facility security clearance.
SOURCE: Homeland Security Today by Matt Seldon – August 8, 2024

As the new school year approaches, the Cybersecurity Alliance has introduced an Anti-Cyberbullying Toolkit designed to help parents, teachers, students, and communities recognize and report cyberbullying. This initiative aims to address the growing problem of cyberbullying, which has become increasingly prevalent in today's digital age.
The toolkit, available for free, includes a variety of resources to support the fight against cyberbullying:
SOURCE: U.S. Department of Health and Human Services – October 3, 2023
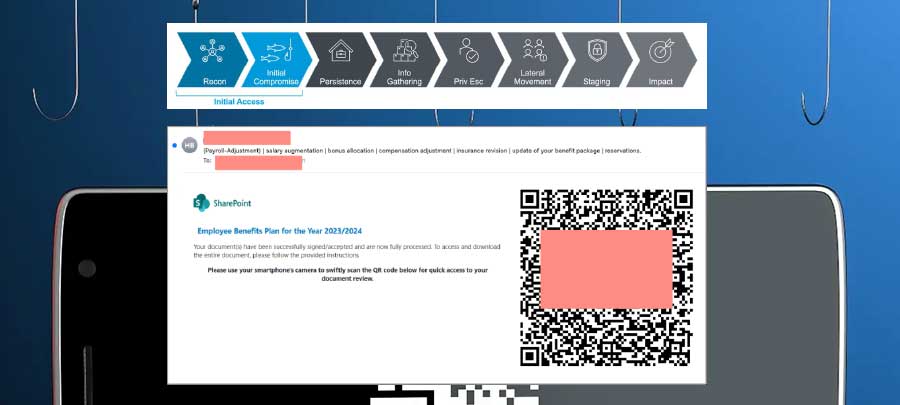
Phishing – the use of phony e-mails to deliver malicious code – has historically been a successful means for cyberattackers to compromise victim organizations and launch full-fledged, multi-staged cyberattacks. Phishing attacks are frequently utilized as the first stage of an attack – the infection vector – and this is especially true for the health sector. A cyberattack that begins with phishing often ends with ransomware and/or a major healthcare data breach. Quick response (QR) codes were designed to quickly read and transmit legitimate data, but have become increasingly abused as part of phishing attacks, called "quishing". In this paper, we provide a brief overview of QR codes, phishing attacks, and the application of both of these to cyberattacks on the health sector. We conclude this analysis with recommended defense and mitigation actions to reduce the likeliness and effectiveness of phishing attacks, including those augmented by the use of QR codes.
A quick response code, or QR code, is a machine-readable image in the form of a matrix that transmits information when scanned by an informaiton system. QR codes connect the digital and physical world, and are frequently used by commercial tracking, advertising and convenience-oriented applications, and are compatible with and often utilized with modern smartphones. The term "quick response" refers to the purpose of a QR code to be scanned in order to access data, and this process happens very quickly. Legitimate QR codes are frequently sent via e-mail and as such, are also abused by those who use e-mail as part of cyberattacks, in the form of a phishing attack.